What Do You Need to Know About A SD-Wan? Traditional WANs rely on physical routers to connect remote users to applications hosted in data centers. These physical routers have two separate planes – a control plane and a data plane. Network administrators and engineers write policies and rules for data flows to determine how the data is routed through these routers. They must do this by hand for every router. An SD-WAN separates management and control processes from the underlying networking hardware. This allows network administrators to write new rules and policies quickly and without requiring in-depth knowledge of networking technology. Learn about sd-wan here.
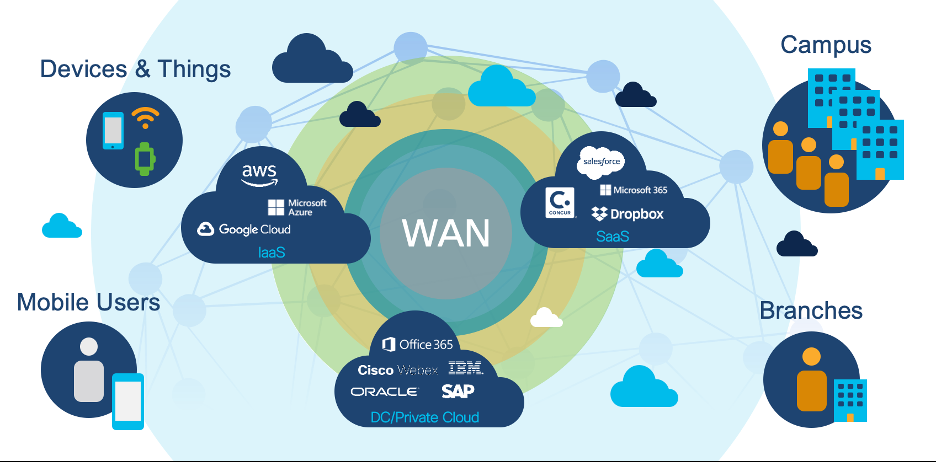
WAN virtualization
Business-driven SD-WAN solutions enable IT, teams to manage exponentially larger volumes of data. This software helps identify issues and optimize traffic steering across the WAN. With its integrated AIOps, SD-WAN solutions simplify network operations. Legacy SD-WAN solutions struggle with cloud adoption, but next-generation solutions can deliver critical branch services from the cloud. Learn more about this technology.
An SD-WAN solution offers improved application performance. This is because it automatically directs traffic to the best possible path by responding to real-time network changes. In contrast, a basic SD-WAN solution is based on templates and pre-defined rules. With a business-driven SD-WAN, changes are made in real-time, which means that the network adapts automatically to meet changing business requirements. As a result, using SD-WAN can improve performance and reduce costs.
Dynamic path selection
SD-WAN uses a policy-based routing method to manage dynamic path selection. Each SD-WAN policy-based route has a corresponding Path Selection Profile that determines which path to take for outgoing traffic. As a result, traffic is load-balanced across the qualified tracks. Without capable paths, SonicOS SD-WAN will disable them. Therefore, you should configure a path selection profile in the SD-WAN to ensure that traffic is routed optimally.
To configure Dynamic Path Selection, enter the following command. First, specify a policy on the VRF and set 4793 as the destination UDP port. Next, apply the DPS configuration to voice, SCP, and FTP application traffic. After you configure the policy, select a WAN link to use. You can also configure the WAN link for Dynamic Path Selection. This configuration will enable the routing policy across all the intermediate nodes.
Another essential feature of SD-WAN is its ability to create quality-of-service (QoS) policies that determine each traffic flow’s priority and quality of service. Business intentions can be implemented as policies through the central management console (CMS), and new and updated policies are downloaded to all the SD-WAN routers and gateways. These policies are used to steer traffic dynamically. Therefore, knowing which procedures you want to apply to your traffic is essential.
Data plane encryption
ASD-WAN devices are capable of supporting Data plane encryption. TLS provides authentication and encryption. Cisco SD-WAN devices exchange digital certificates to identify themselves and ensure traffic integrity. Digital credentials are hard-coded into the devices or installed via software. The AES-256-GCM encryption algorithm is used to ensure data integrity. Cisco SD-WAN devices can also provide DTLS support. However, it is not mandatory.
Control plane security is crucial to the SD-WAN. DTLS, based on the TLS protocol, encrypts traffic, validates data integrity, and ensures confidentiality. It also uses symmetric encryption, message authentication codes, and critical exchange to protect data integrity. Cisco SD-WAN software implements the standard DTLS with UDP and TLS. While these security features are helpful, it’s important to remember that they have their limitations and can’t be used in all situations.
The Cisco SD-WAN data plane is built on a secure control plane that authenticates all the edge devices. It can also provide specific data paths. The vEdges’ identity is established with the vBond orchestrator during the provisioning process. The WAN edge routers then advertise their key to the vSmart controller, redistributing it to all peers. The vSmart controller then validates the keys and makes the network secure.
Zero-touch provisioning
Zero-touch provisioning (ZTP) is a technology that enables networking appliances to be installed without local configuration. This allows local employees, even those without IT training, to install new or replacement devices. When a new device is installed, the ZTP feature performs the configuration and connects to a management system to perform other administrative tasks. Zero-touch provisioning also helps to keep IT costs down.
A secure zero-touch solution allows for easy deployment and configuration. After the design is complete, the SD-Wan device will automatically connect to the Cloud Portal, authenticate, and add itself. Zero-touch provisioning can also make it easy to deploy new devices in minutes. Zero-touch provisioning also helps reduce the need for manual intervention, which saves money and time for IT teams. However, this feature is not available on every SD-WAN device.



